The new Cybersecurity Maturity Model Certification (CMMC) framework was presented in January of 2020, which details tiers of cybersecurity best practices, which all 300,000 members of the Defense Industrial Base […]
CMMC: What You Need To Know


The new Cybersecurity Maturity Model Certification (CMMC) framework was presented in January of 2020, which details tiers of cybersecurity best practices, which all 300,000 members of the Defense Industrial Base […]

As more and more people begin working from home and utilizing new video conferencing software. Hackers are finding more and more ways to unsuspecting users into giving up user data. The […]

By now most of us that can do so have been asked to setup their home office and begin working from home to maintain productivity. That means we will be […]

Teleworking opportunities have become increasingly more favorable in today’s world, with an increased list of benefits for both employers and employees. Reduction in overhead costs, reduced commute time, zero judgment […]
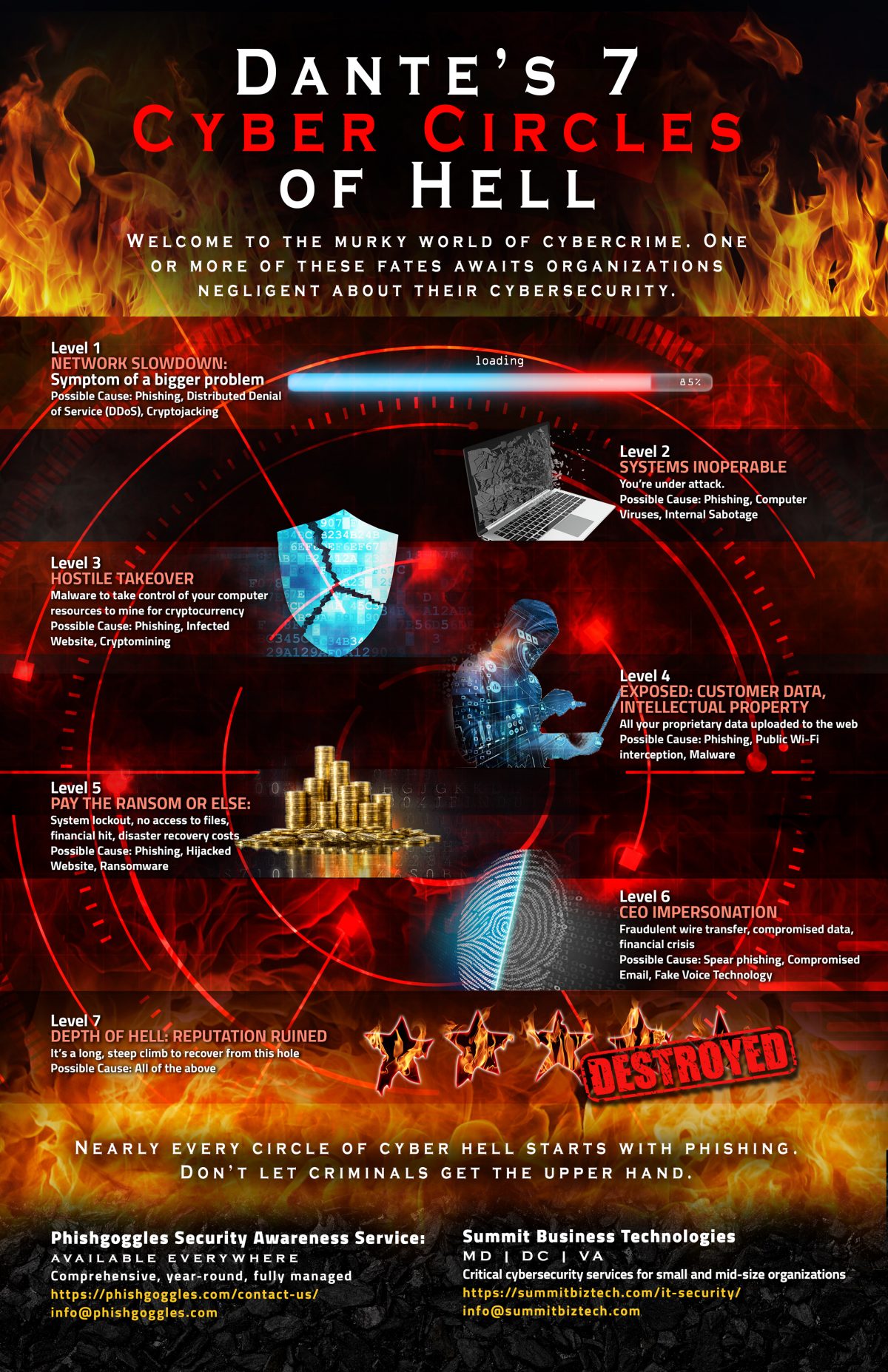
If Q4 isn’t stressful enough for organizations, cyber criminals will make sure it is. The near constant occurrence of cyberattacks ramps up even more in advance of Halloween and the […]

Read Our Guide: How to Choose the Best Office Phone System The quick guide discusses: Landline Systems VoIP on Premise Solutions Cloud Based VoIP Systems Find out the questions […]

Bogus retail sites, extreme discounts, busy hackers The National Retail Federation expects 115 million physical shoppers to be out on Black Friday, and cyber crooks want a part of the […]
“Dogfooding” or eating your own dog food: a term used to reference a scenario in which a company uses its own product to validate the quality and capabilities of the […]

Have Questions? Get the guide. Office moves can be difficult scenarios in which technology gets left behind or incorrectly configured. Are you prepared to safely transport all data? Is there […]

Mind Your Manners You can tell a lot about a work environment by its videoconference etiquette. How often have you been subjected to people trying to unobtrusively text, or worse, […]