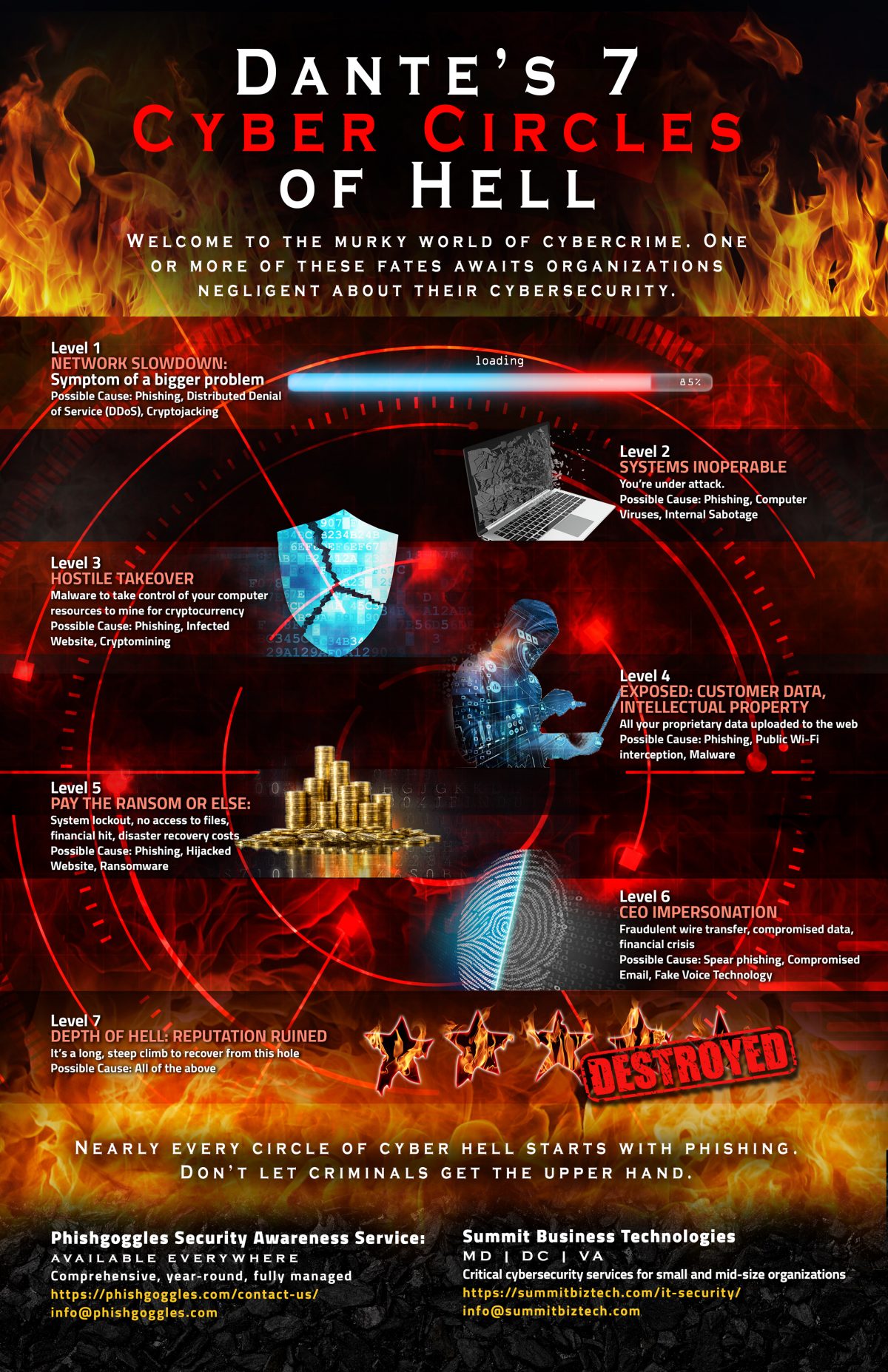
The new Cybersecurity Maturity Model Certification (CMMC) framework was presented in January of 2020, which details tiers of cybersecurity best practices, which all 300,000 members of the Defense Industrial Base (DIB) will need to be certified in. As of the writing of this article, the AB is still finalizing the criteria to certify the auditors […]
CMMC: What You Need To Know