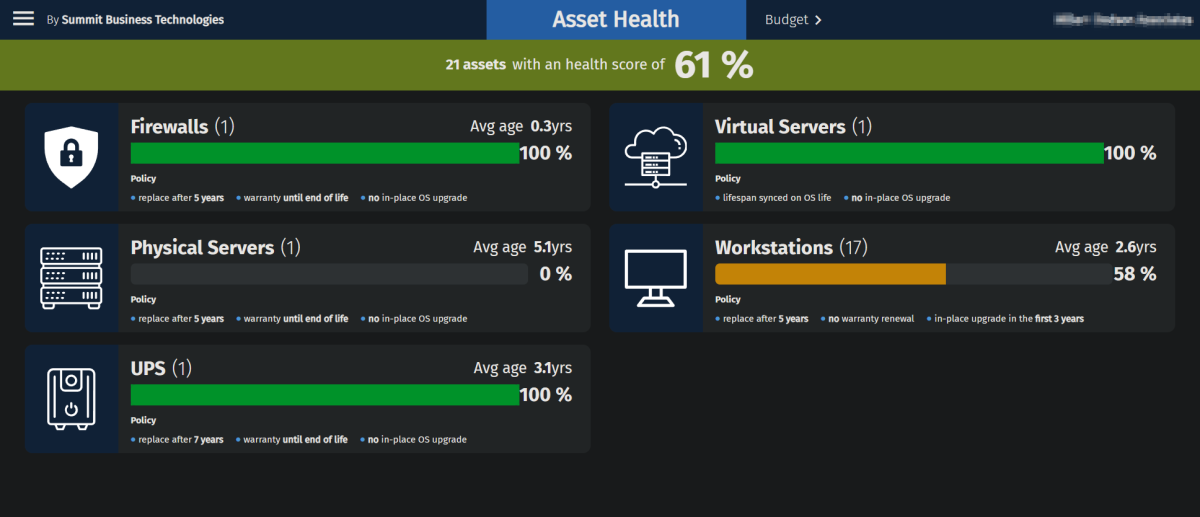
The Enemy Within The enemy is sometimes from within. When most organizations think of cybersecurity threats, they think of external criminals but never an internal employee. In an article from earlier this year linked here, we learn about a case out of Singapore where a disgruntled employee deleted all 180 test servers after he was […]