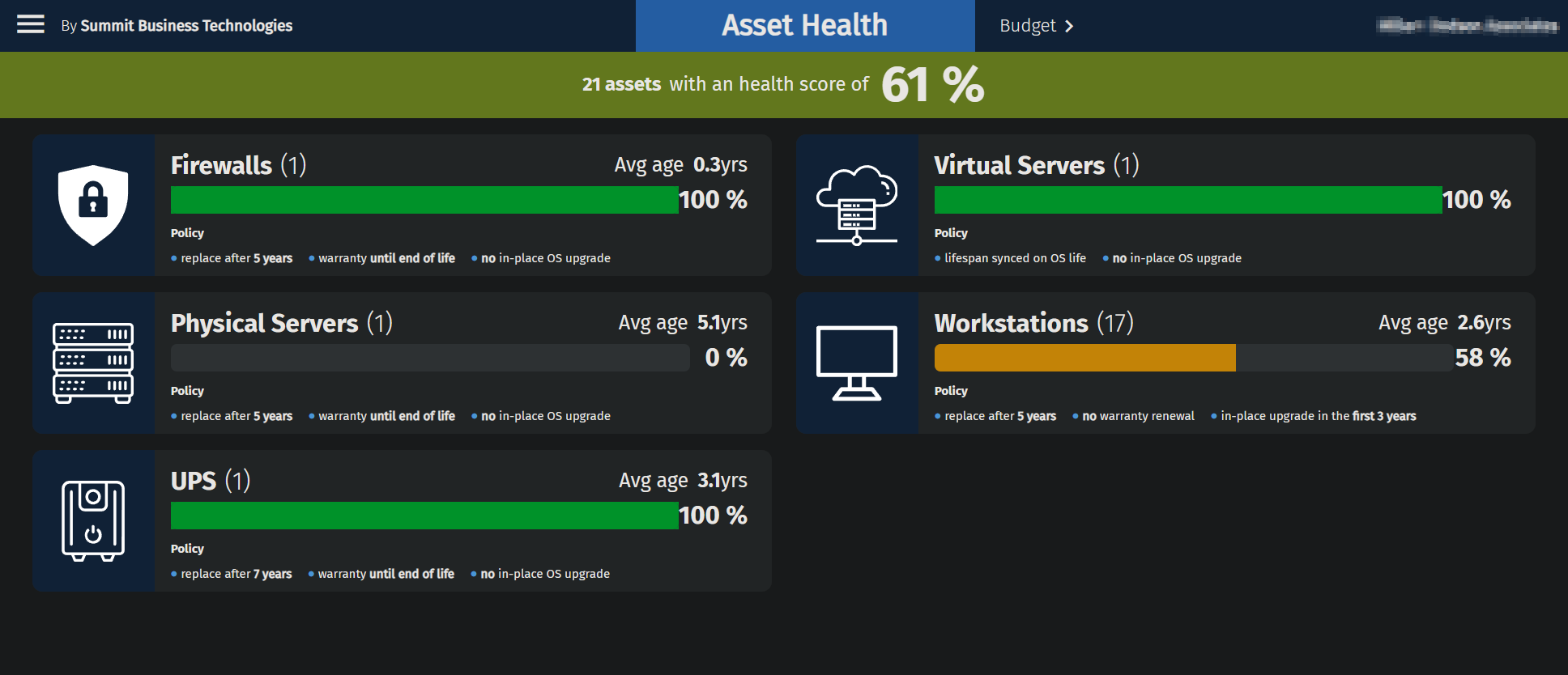
The Benefits of Business Reviews with Summit
At Summit, we believe in the power of regular Business Reviews to keep your IT systems running smoothly and your business thriving. Here’s how these periodic reviews can benefit you: A Clear Picture of Your IT Status Business Reviews give us a chance to assess the current state of your IT systems. By taking a step back to look at the big picture, we can spot what’s working well and identify areas for improvement. This proactive approach










