In today’s digital landscape, organizations face an ever-increasing number of cyber threats. With the average cost of breach remediation being over $1.45 Million, a successful data breach could spell disaster. To protect sensitive information and maintain business continuity, organizations must understand the threats in front of them, and implement effective risk mitigation strategies to help combat and reduce the risk of a breach.
Understanding Cybersecurity Risk
What is cyber risk? Cyber risk is the possibility or risk of potential harm an organization faces due to cyber threats. Bad actors, both external and internal to your company, look to exploit vulnerabilities in systems, processes, or people. The goal of a cyber risk mitigation strategy is to reduce the likelihood and or the impact of these threats.
Cybersecurity Risk Mitigation Strategies
Risk mitigation strategies fall into one of four categories: Accept, Avoid, Transfer, and Control. When building a resilient cybersecurity infrastructure and properly mitigating a threat or risk, the first step is to identify the threats your organization may face and classify any response into at least one of these categories.
Acceptance: These are threats and risks that cannot be adverted, and an organization must accept the threats and monitor them to minimize the damage they may cause. Things like allowing your employees to access and store sensitive data from time to time is part of doing business and therefore cannot be avoided.
Avoidance: Threats and risks that you aim to avoid and eliminate fall into this category. Anti-virus software, Spam filtering that blocks potentially suspicious emails and DNS filtering that blocks access to dangerous websites, are all ways to avoid threats and reduce possibility of an employee being compromised.
Transfer: Another effective mitigation strategy is transferring the risk to a third party completely. Storing your data in a secure cloud, employing a third-party team to monitor and support your data security or purchasing cybersecurity insurance. All of these are options available to reduce the risk or the cost of remediation should a breach occur.
Control: Similar to acceptance, some risks are inevitable with doing business throughout your day. However, rather than simply accepting the risk, you actively work to control the threat. Minimizing user access, enabling, and configuring MFA (Multi Factor Authentication) or SSO (Single Sign On), and utilizing different security software allows you to control and reduce the possibility of a successful breach.
NIST Cybersecurity Framework (NIST-CSF) 2.0
Once you have a grasp on the risks and strategies available to you. The next step is enacting a plan and designing a robust security stance, which is where the NIST- Cybersecurity framework or NIST-CSF 2.0 comes into play. The NIST-CSF provides a structured approach to managing cybersecurity risk. It consists of 6 core functions that provide the building blocks to develop your risk mitigation strategies and infrastructure:
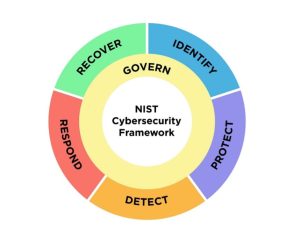
- Identify
- Understand and manage cybersecurity risks. Identify critical assets, threats, and vulnerabilities.
- Protect:
- Implement safeguards to protect assets. This includes access controls, encryption, and security awareness training.
- Detect:
- Continuously monitor cybersecurity events. Detect and respond to incidents promptly.
- Respond:
- Develop an incident response plan. Coordinate actions during and after a security incident.
- Recover:
- Restore normal operations after an incident. Learn from the experience and improve resilience.
- Govern:
- The newest of the core functions details that organizations need to have a plan in place that is regularly reviewed for accuracy.
When used properly, the 6 functions of the framework will help you develop the strategies needed to secure your data and reduce the possibility of a data breach. It also helps organizations develop contiguous plans that can be enacted should a disaster strike. Having a plan in place allows an organization to reduce the scope of a breach and potentially recover and get back to business as usual quicker.
How can Summit help?
Effective risk mitigation is critical for businesses and organizations regardless of size or industry. By combining the strategies mentioned above and aligning with frameworks like NIST-CSF, organizations can enhance their cybersecurity posture and safeguard critical assets reducing the possibility of a breach occurring.
For some organizations understanding the framework, strategies and tools can be outside your internal employees’ ability. By working with a MSSP (Managed Security Service Provider) like Summit, we can assess your organization, develop, and enact the risk mitigation strategies, policies, and procedures you need to stay safe. If you are interested in learning more about either risk mitigation or the NIST-CSF, click on the link below to set up a free consultation.
Remember: Cybersecurity is everyone’s responsibility. Stay informed, stay vigilant, and prioritize risk reduction.