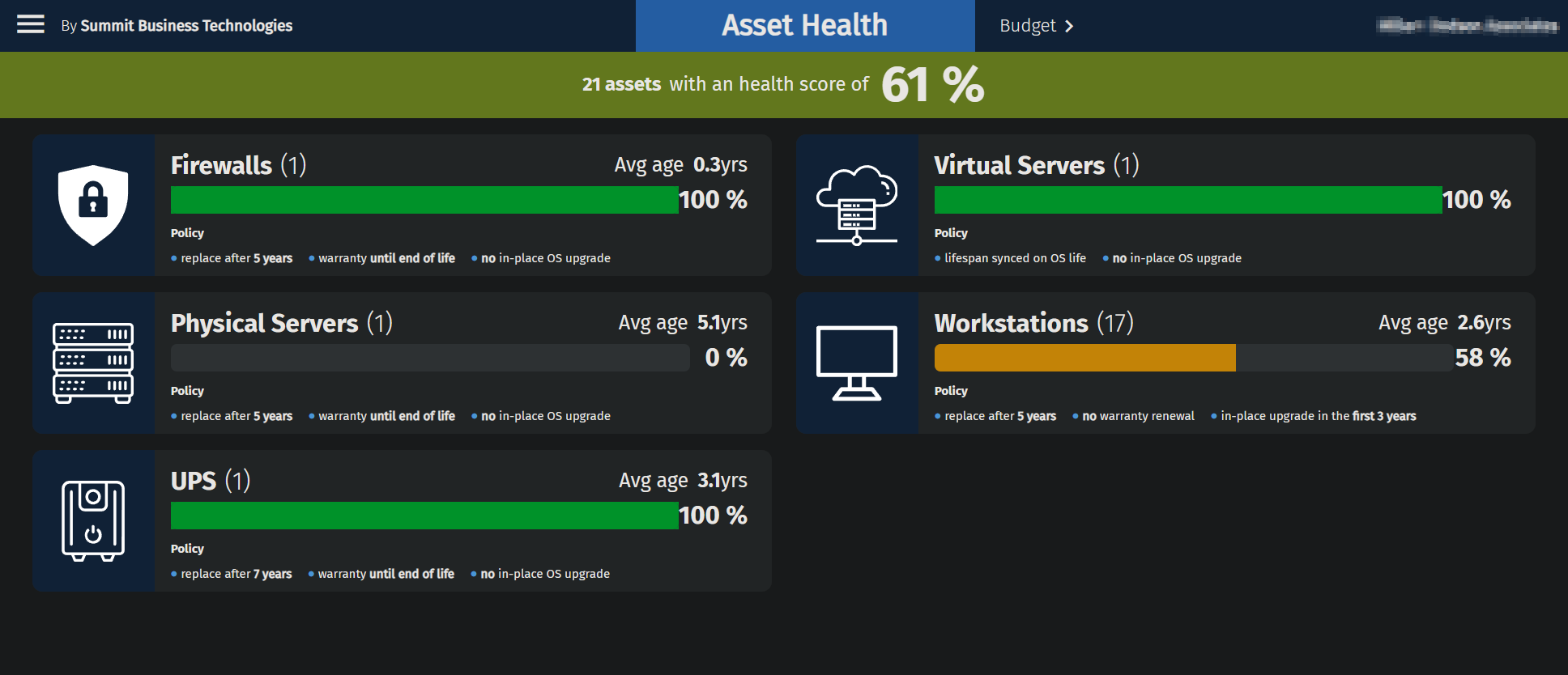
Top 5 Cybersecurity Resolutions for 2025
As we head into 2025, it’s time to focus on strengthening your business’s defenses against ever-evolving cyber threats. Start the year off right by committing to these top five cybersecurity resolutions that will protect your business and your bottom line.