Register Here:
Join Webinar
https://us02web.zoom.us/j/82077585141?pwd=c2p6b2x4UmppYTZ4T2NRaEg1LzExUT09
Meeting ID: 820 7758 5141
Passcode: 412490


Join Webinar
https://us02web.zoom.us/j/82077585141?pwd=c2p6b2x4UmppYTZ4T2NRaEg1LzExUT09
Meeting ID: 820 7758 5141
Passcode: 412490
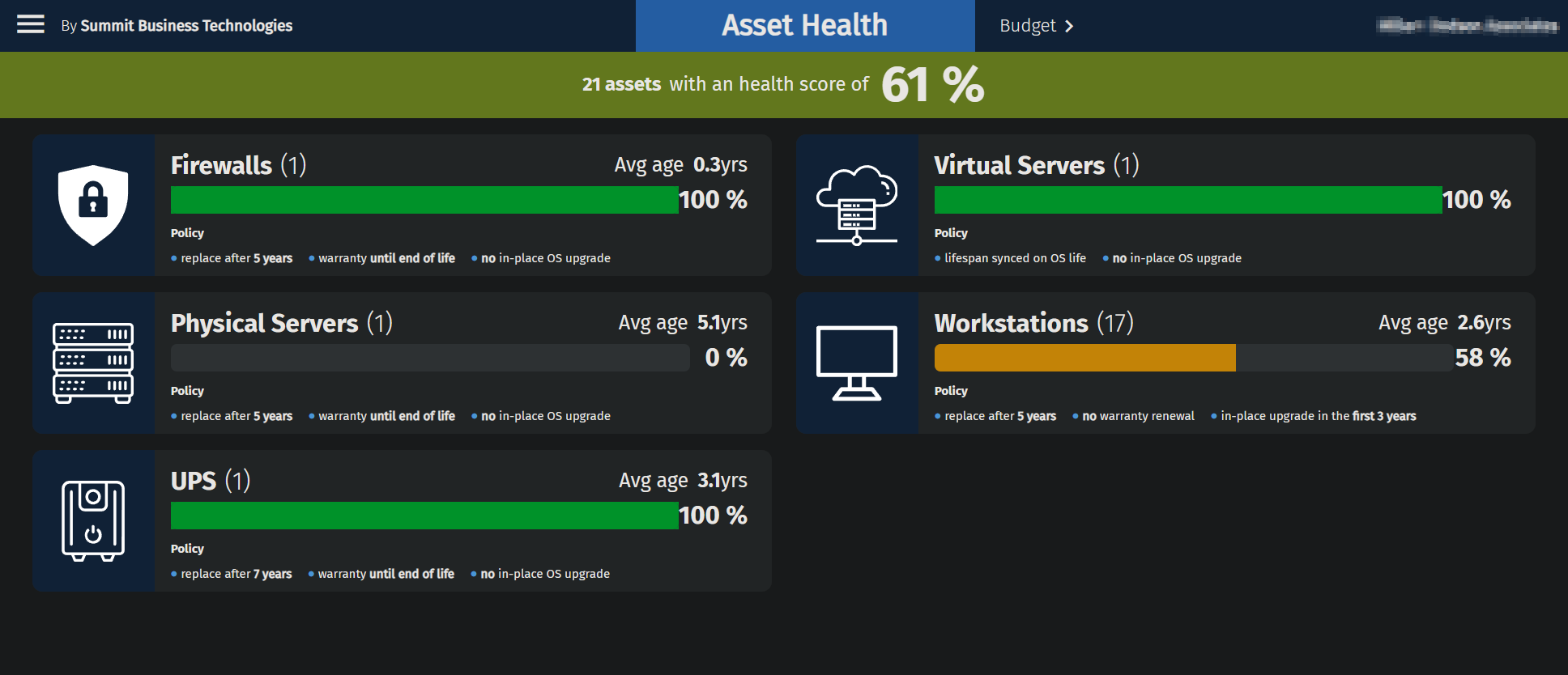
At Summit, we believe in the power of regular Business Reviews to keep your IT systems running smoothly and your business thriving. Here’s how these periodic reviews can benefit you: A Clear Picture of Your IT Status Business Reviews give us a chance to assess the current state of your IT systems. By taking a step back to look at the big picture, we can spot what’s working well and identify areas for improvement. This proactive approach

Traveling expands your horizons and offers new experiences but also brings new cybersecurity risks. Whether you’re traveling for work or leisure, staying alert about your digital security is vital. At Summit, we’re committed to protecting our clients and their businesses from cyber threats. To assist our clients while they’re on the go, we’ve put together some essential tips for staying cyber-safe while traveling. Before You Depart: Pre-Trip Preparations Create a Backup: Before you set off, back up your data to

Is Your Staff Getting Regular Security Awareness Training? Studies show that the most successful cybersecurity breaches continue to be the result of human error. From clicking on malicious links and attachments to misconfigured systems and easy to guess passwords, the human factor remains a vulnerability that organizations need to address. As technology changes, so do the tactics of those with malicious intent, making it imperative for organizations to invest in regular security awareness training for their employees. Why Regular Training

In today’s digital landscape, organizations face an ever-increasing number of cyber threats. With the average cost of breach remediation being over $1.45 Million, a successful data breach could spell disaster. To protect sensitive information and maintain business continuity, organizations must understand the threats in front of them, and implement effective risk mitigation strategies to help combat and reduce the risk of a breach. Understanding Cybersecurity Risk What is cyber risk? Cyber risk is the possibility or risk of potential harm

For businesses, Software-as-a-Service (SaaS) solutions like Office 365 and G-Suite offer opportunities to enhance efficiency, scalability, and overall operations when it comes to file management. However, because your files are stored in the cloud, many believe that cloud backups are no longer needed. This generates a growing number of backup-related misconceptions, which have the potential to hurt your business growth. Don’t let these 3 myths put your business at risk Myth 1: My SaaS solution is completely secure.