CMMC 2.0 What are the changes to CMMC
In January of 2020, the DoD issued a new standard that the Defense Industrial Base (DIB) needed to adhere to be eligible to bid on ANY contract with DFARS requirements. This standard known as the Cybersecurity Maturity Model Certification or CMMC, would become the law of the land. This standard listed and added additional controls and requirements needed to be in place to have what the government considered a sufficient cybersecurity infrastructure capable of securing CUI. This standard was set to replace NIST 800-171.
WHAT IS/WAS CMMC?
We have posted about CMMC on a few occasions for a more in depth description of the standard feel free to review our previous blogs HERE and HERE regarding the CMMC standard.
In short, CMMC was a certification process that ensured defense contractors were meeting the necessary controls to secure Controlled Unclassified Information or CUI. It consisted of 5 different levels with increasing lists of controls that needed to be in place prior to winning a defense contract.
Defense contracts would have a minimum CMMC Maturity Level that they need to be certified to. These companies would need to be audited by a third party to receive a certification from the Accreditation Body prior to the contract award.
CMMC 2.0? What’s New?
After an extensive internal review process by the DoD, a new standard was written, dubbed CMMC 2.0. This update came with a few major changes to the standard.
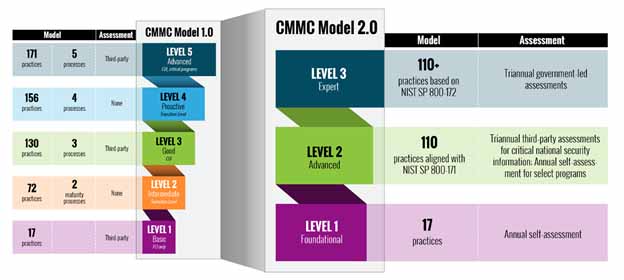
While we do not want to oversimplify things at this time, it is important that we highlight some of the key differences between CMMC 1.0 and 2.0.
- Removal of levels 2 and 4. This drops the number of levels from 5 to 3 and allows for alignment to established NIST standards. With level 1 being self-attestation only.
- Removal of maturity level requirements.
- Addition of POAM for non-high level requirements and a minimum score to be considered complaint. POAM items will need to be completed in a 180-day timeline
- Roll out timeline is expected to be 9-24 months
While these few items highlight some of the larger changes being made to CMMC it is important to remember, these changes are still unofficial and will need to be finalized and approved before being put in place. However, assuming these changes do stand as they are currently list, what does this mean for the Defense industry? We’ll attempt to break down some of the updates below, however for a more detailed description we recommend giving us a call to discuss the updates.
What do the updates to CMMC mean for the Industry?
First and foremost is the simplification of the standard itself. Gone are levels 2 and 4, this removal streamlines the standard and aligns the levels with established NIST standards. This streamlines the standard considering that most contracts were expected to require meeting levels 1, 3 or 5 and that levels 2 and 4 were never clearly defined.
Secondly is the removal of the “maturity level.” Under CMMC v1.0, companies would be required to show “a significant cultural shift” after the adoption of the controls of CMMC. This would require logs of the controls being in place for an unspecified period, but most believed the requested period by auditors to be approximately 6 months. By removing the maturity level, this allows smaller and newer companies looking to enter bidding on defense contracts a quicker turn around on their ROI. However, while the maturity levels have been removed from CMMC at this time, there is potential for them to be implemented through the underlying NIST standards.
Third, is the addition of allowing companies to have a POAM (Plan of Actions and Milestones) with a finite timeline. In CMMC v1.0, companies would need to be compliant with ALL controls of CMMC for a period before receiving their certification and then being able to bid on defense contracts. Failing to meet a control could preclude a company from receiving their desired CMMC level certification and therefore preclude said company from bidding or renewing a contract. By incorporating a POAM into CMMC 2.0 allows companies who may not have completed all controls to potentially earn their desired certification level, provided said company completes the items in the required timeline. One item of note, currently only certain controls will be eligible to be included on the POAM while others will be required to be completed prior an audit. This list of eligible controls may change prior to the standard finalization.
Last is the rollout timeline of 9-24 months. The previous timeline for CMMC was a 5-year rollout starting in 2020 with an expected full roll out of CMMC in all contracts by 2025. With CMMC 2.0, the new timeline has been shortened significantly to potentially less than half the original rollout timeline. What we do not know currently is this- is the 24-month timeline when the new rollout will begin or is that the planned rollout completion?
How can Summit help?
While we wait for the final changes to be accepted through the rule making process the DoD has put a hold on adding any new CMMC language to any other Defense contracts. However, that does not mean that you shouldn’t be preparing for the future. NIST 800-171 is still current standard and the basis for CMMC LVL 2. Also, current DFARS contracts require attestation to NIST 800-171 compliance and the submittal of your SPRS score to the PIEE website. Ensuring that your firm is complaint to NIST 800-171 will put in you in a good place for when CMMC 2.0 is finalized and goes into full effect. At Summit, we can walk you and your team through a full assessment against the NIST 800-171 standard and offer you recommendations to remediate and fill any gaps that we find in your Cybersecurity infrastructure.
If you would like to schedule a call to learn more about our NIST 800-171 assessment process and some of the options we have to help reduce your security risk, or if you would like to discuss the updates and what they mean for your company, click on the link below to schedule an appointment with a member of our team today.
https://meetings.hubspot.com/ken-cikanovich






