What is Multi-Factor Authentication (MFA)?
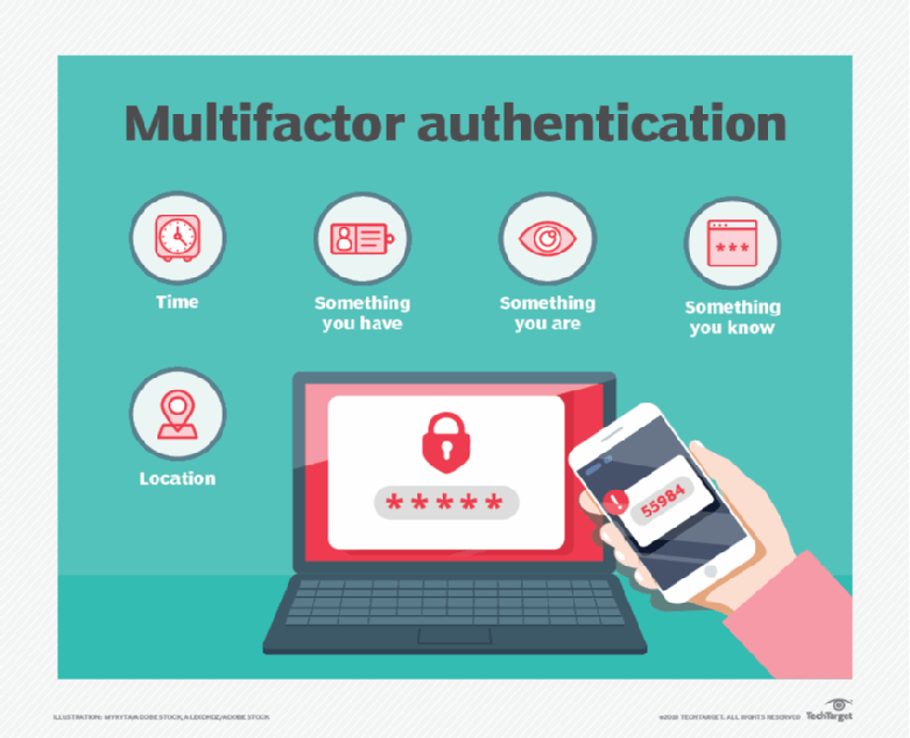
MFA is a security measure that requires multiple types of credentials to verify a user’s identity prior to accessing an account or system. When a user logs in with a username and password, one or more additional forms of identification will also be required before allowing access.
The key that makes MFA effective is the systems typically require information that hackers are not likely to have. While they may be able to steal your password and/or login information, it’s not as likely that they will have also have access to your phone or be able to obtain your fingerprint.
That’s why MFA requirements will often involve generating a one-time code, either through a phone app, physical key fob or using biometrics such as fingerprints or facial recognition.
Microsoft reported that MFA can prevent over 99.9% of account compromise attacks. For such a simple tool yielding such an effective result, there is no reason for every business and employee not to be using MFA.
Hackers typically target login information through some basic cyberattacks. Some of the more common cyber-attacks that target login information are below:
- Phishing: Often disguised as a trusted organization, the attacker delivers a message to a list of phone numbers or email addresses, usually with a call to action which requires login information and a fake website where the user is expected to provide that information.
- Spear Phishing: Like phishing, but it is targeted at a specific group of people using personalized messages. Criminals may glean information from social media accounts or other sources to personalize these messages and make them appear more trustworthy.
- Keystroke Logging: The attacker installs a program (usually a virus) through a malicious email attachment that captures keystrokes from the user’s computer, including passwords, sites visited, and usernames.
- Credential Stuffing: The attacker relies on the user repeating usernames and passwords to log into their applications and sites. They attempt to use one set of stolen credentials to gain access to additional sites and programs.
- Brute Force and Counter Brute Force Attacks: The attacker uses software to rapidly test a variety of common credentials (e.g., Password123) to gain access to sites and applications.
- Man-in-the-Middle Attacks: The attacker accesses a user’s connection to another party, then either observe the interaction or redirects the connection to a fake site where the user will enter their login information.
Each of these attacks is focused on one thing, obtaining a user’s username and password. However, utilizing MFA can help thwart a breach should credentials be obtained by a criminal. If your username and password is compromised, the criminal won’t be able to obtain your MFA code unless he also carries out a sophisticated attack like swapping your phone’s SIM card or intercepting and decrypting your connection to the website.
Increasing Cyber Attacks and Security in a Digital Age
According to a study from the University of Maryland, there is a hacking attempt every 39 seconds, affecting every one in three Americans yearly. And 43% of all cyber-attacks are directed at small businesses.
These numbers only prove that the digital age with all its advantages has also introduced greater risks, and both businesses and individuals must go the extra mile to protect themselves.
Due to the pandemic, remote work is rapidly becoming more prevalent, unfortunately, has become a focus for hackers. That is because, without secure connections set up before going remote, employees’ devices and networks are more susceptible when they are not under the protection of in-office systems. Cybercrime is up 600% due to COVID-19 pandemic.
With this sobering information in mind, you need to ensure that your business prioritizes security over convenience when it comes to protecting company data by using MFA and other security measures.
Don’t Leave Your Business Unprotected
No matter what industry you are in, you need a strong cybersecurity plan in place to protect your information and assets. Multi-factor authentication is an extremely important first step, At Summit we have several options that can be implemented depending on your business’ needs. Book a time with our sales team to discuss how we can help.